RusGas: Timeline of an ICO Token Scam, Exchange Dump, and Weak Coverup
UPDATE: On December 6th, we received reply from the Crex24 team “Our current policy is to act according to coin/token dev requests. As they have their own (and, we hope, the best) vision of coin/token promotion/development.” Crex24 will not disable trading despite being fully aware of the situation. It is now our opinion that Crex24 are knowingly profiting from fraud and are complicit in this scam.
On November 28th, 2018, MonitorChain detected the latest incident in a seemingly endless stream of ICO token fraud. RusGas, an ICO that claims to have raised over $2.2m USD from investors in Spring 2018, minted 100 billion new tokens, an 11 fold increase on their total supply which had previously been set to 10 billion. Such a drastic unexpected mint event immediately triggered the highest alert levels of MonitorChain.
Within a matter of hours, the vast majority of these newly minted tokens were sent to the wallet of the Crex24 exchange. As often happens following smart contract exploits and exit scams, these tokens were sold on Crex24, leading the little known RusGas token to be the highest volume traded asset on the exchange for the day, with over $350,000 USD worth of volume. What makes this unique versus other similar exchange dumps is that is took advantage of the already extremely low price of the RusGas token. Even prior to this incident, the entire supply of RusGas had a market cap in the region of the tens of thousands of dollars, with individual tokens hovering around the lowest possible price supported in the exchange. This allowed those dumping the minted tokens to sell massive volumes without lowering the price. It is highly possible that bots not detecting the supply increase would be tricked into buying these tokens. Based on this combination of factors, hundreds of thousands of dollars worth of Bitcoin were able to be extracted from exchange users on a token with a tiny fraction of that even before the supply change.
Noting this, we published our findings the following day:
RusGas, a $2.2m ICO from earlier this year, minted 100billion new tokens yesterday, increasing supply by 10x. Most of these tokens have been sent to the Crex 24 exchange, where 60BTC worth have been traded today @crex_24 @rusgasofficial
— Zenchain (@ZenchainGroup) November 29, 2018
Theft and hacks are an unfortunate fact of life in cryptocurrency, despite the best efforts of auditors and developers. What is not acceptable is the horribly inadequate manner that they are handled by token teams and exchanges. On December 1st, a full 3 days after the mint event, the RusGas team left a vague post on their Medium blog and website homepage that attempt to play off this event as an upgrade, completely omitted the massive mint and losses suffered by traders.
Further investigation into the incident only makes things look much worse for those involved. The tokens were minted by the same original owner of the token, meaning that this event was either done by the RusGas team themselves, or by someone who managed to gain access to the private keys of their admin account. Even though the smart contract of the RusGas provides possibility to finishMinting, they have never set that property to true, after the initial crowdsale. This simple action, that was fully within control of the RusGas team, would have prevented this entire security fraud from having occurred. Several smaller mint events in the previous months indicate that this could have been a long running scam that did some small test runs earlier before the drastic fraud of the past week.
There can be no denying that these tokens have hit the order books of Crex24, who, despite our attempts to bring the situation to their attention, continue to allow trading on the RusGas token at the time of publication. On December 4th a further 250 billion RusGas tokens were minted, and there are now over 170 billion RusGas tokens in open sell orders on the Crex24 order books.
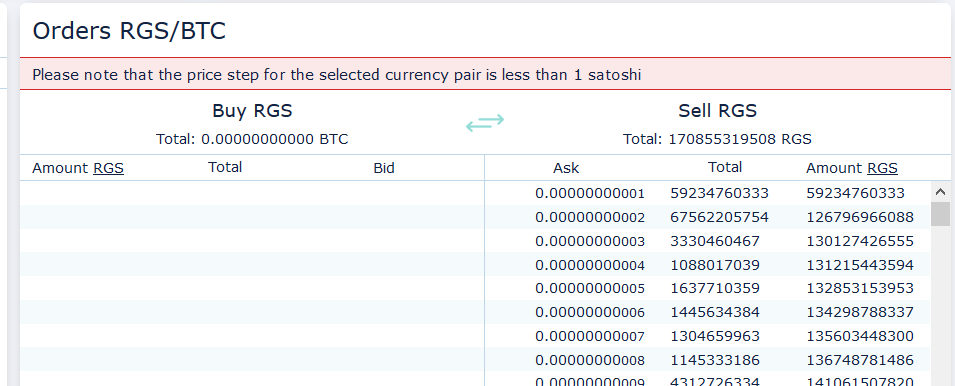
In total, this event has now involved over $500,000 USD in total volume, much of it can be assumed to have come from unsuspected Crex24 traders who manually or algorithmically purchased these tokens unaware of its supply increase which now stands at 36 times the ICO supply cap. The most appalling aspect is that a full week after the massive mint, trading of RusGas is still active on Crex24.
MonitorChain continues to reach out to the Crex24 team and hope that trading will be suspended before further losses are suffered. In all, this event leaves another black eye on an ICO space already reeling amidst numerous challenges. For exchanges and token teams that wish to protect their users and investors from incidents such as this, please contact us to discuss our automated security solutions.
